This site uses only a few technical cookies necessary for its operation. By continuing to browse, you accept their use.
To find out more...
To find out more...
20 measures to protect your privacy
19 K 4.0/5 (45 reviews)
Last modified on: April 16th 2013
20 measures to protect your privacy

For instance, when we use the internet, we need to be wary of what is collected about what we do, our habits, etc.
Here is a list of simple measures which allow us to reduce the natural “vulnerability” of our data:
Internet

- Protect: Use a strong password whenever you are asked for one. You can see some advice about this here.
- Keep secret: Never forget that a password is as personal as a handkerchief or toothbrush – never, ever, share it with anyone else, even someone you trust (who might be negligent or take this less seriously). If, however, you do ever need to let someone else know your password, change it immediately after this “loan” is finished.
- Double up: Set up an email address to use for anything that requires you to give your email address (online shopping, forum membership, signing up to anything, etc.). Only use your main email address for serious business and real contacts (family, friends, professional, etc.
- Camouflage: When you create this “commercial” email address, throw them off your trail: if you are asked for details of your age, sex, country, address, etc., give fantasy details that are completely different from your real ones: invented date of birth, false name, even change your sex.
- Separate: Still on the subject of this commercial email address, never choose the same password that you use with your main address. If you are asked for a backup email address in case you lose your password, do not enter anything, or at the very least, never enter your main email address.
Log out: Do you use an online service that requires you to log in (Facebook, Twitter, Google, etc.)? If so, never tick the box that says “keep me logged in” and, most importantly, always log out afterwards. Whenever you stay logged in, you give information about your online behaviour to the service in question. If you would like a quick demonstration of this, do a Google search of your name: do exactly the same search logged in, then logged out and see the difference.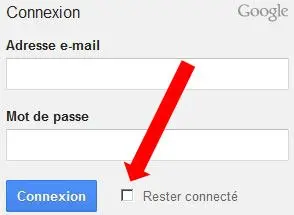
- Clean: Have a regular clear out of all the cookies stored in your browser's memory. If you have not done this for a while, you will be amazed at how many there are and the number of sites that have deposited one.
- Observe:
Install a tool in your favourite browser to identify trackers hidden in web pages you visit, so that you can block them if you wish. Example: Ghostery in Firefox – the number of trackers on some pages will leave you open-mouthed (10 or more different ones). - Be paranoid: Use the “in private” or “incognito” option of your browser whenever you have any doubts about a site, or if you prefer to do certain things discreetly, without leaving any traces on your computer. But you should be aware that this mode does nothing to prevent data being recorded on the server you are visiting, nor – importantly – the proxy through which you are passing. To quote Gordon Moore (former Intel CEO): "Only the paranoid survive".
Conventional mail

- Use the same weapons as the enemy: If you are asked for your postal address in an online form and you are obliged to give it, then add your own “tracker” . Then, if you receive junk mail one day, you will see where your address has been harvested from. A tracker in this case is some sort of useless “padding” detail added to your address, which does not affect postal delivery, but is a clue for you: for instance, add "block XX" ou "yy floor" (when this does not really exist where you live), or slip in a little deliberate spelling mistake, or even add "c/o Mrs. So-and-so", etc.
- Send it back: Have you received commercial junk mail? Don't throw it away, don't open it, but cross out your address and add “return to sender” before posting it again. This will cost the sender money, and they are likely to cross you off their list, especially if you do this a number of times.
- Destroy: Have you received other unwanted mail? Don't just throw it in the bin as it is; it contains data about you (even if it is only your address). It is better to destroy it (tear, shred or burn it). Do this for all personal documents which you no longer need (bills, bank statements, etc.) to protect you from identity theft.
Mobile phone

- Be prepared: What would happen if I was suddenly deprived of my phone (breakdown, theft, loss)? To avoid a full-blown drama, it is better to ask yourself this and prepare for the worst while you still have it in your hand. In particular, take steps to back-up your list of addresses, any important files it might contain, etc.
- Complicate: Don't use a PIN that is too obvious (0000, 1234 or your date of birth), as these are the first things any thief will try.
- Note: Make a note of your phone's IMEI number and keep this somewhere safe (not on the phone itself). This 15-figure number, unique to your phone, is a useful reference if it is lost or stolen. This is also one of the first things you will be asked for when you report the problem, so that it can be blocked remotely. You can find the IMEI number on your phone's outer case, or on the bill, and it is usually on a label under the battery. You can also see it by entering *#06# on the phone's.
- Don't hide: Don't conceal the number you are calling from, as this might arouse suspicion (especially for professional calls) and the person you are calling might well not answer. Hidden numbers are the stock-in-trade of call centres, automatic dialing machines and sales calls. Don't answer any such calls yourself, as this is an underhand practice. If the call is from a call centre or automatic dialer, simply picking up will validate your number on the machine's list (and it will call you again sooner or later). If the call really is for you, the person will leave you a message.
- Think "national": You see that a call is from abroad (beginning with 00XXX), but you don't know anyone in that country: you should treat it like a hidden number and not answer.
- Check: Have you ever received a text message which leaves you a number to call, something like: "Lucy has left you a message, call XX XX to hear it", or "You have received a text message, click on this link to read it or call xx.xx"? This is a very common scam: you will be calling a premium rate number – for nothing, needless to say. The only number you should call is that of your own voice mail; any other is sure to be a fake.
- Unlock: When you have had a new phone for 4 months (usually, but do check with your network provider) remember to "unlock" it, i.e. remove the protection that stops it functioning with another network's SIM card. This will allow you to pass it on or sell it more easily, or keep it as an emergency back-up phone. Remember to do this while the phone is still on the original network contract, as it is more difficult, if not impossible, to do it later. To unlock your phone: note the IMEI number and call your network's customer services. Based on this number, they will give you an unlocking code and the steps to follow to enter this on the phone.
- Recycle: Like most people, you probably have a box at home, full of old phones and chargers that you haven't used in ages. It is a good idea to take these to a recycling centre and only keep your last phone, unlocked, with its charger, in a plastic box or bag. But do be careful: before recycling, check that you have not left a SIM card in the phone and that you have deleted everything (contact numbers, call history, messages, documents, etc.).
That's a quite a lot, I know, but I hope that you will find some useful ideas here to help you protect your privacy as far as possible.
Lasts posts
XO Cognac Explained: Meaning, Aging, and Flavor Profile
XO Cognac always goes beyond the labels on the bottle: it is often associated with tradition and quality. You get to appreciate the artistry, character and ageing process when you understand what defines this smooth Cognac. The section below tackles everything about XO Cognac, from complex flavour...January 28th 20261,165 Sponsored article
Butter vs. grease
We often read in a recipe where a pastry is put into a mould that, just before pouring, the mould should be buttered or greased. But what's the difference between these 2 terms?December 1st 20252,7245
Getting out of the fridge early
Very often when you're cooking, you need to take food or preparations out of the fridge, to use them in the recipe in progress. There's nothing tricky about this: you just take them out of the fridge and use them, usually immediately, in the recipe. But is this really a good method?November 24th 20251,7325
Who's making the croissants?
When you look at a bakery from the outside, you naturally think that in the bakery, the bakers make the bread, and in the laboratory, the pastry chefs make the cakes. It's very often like that, with each of these professions having quite different ways of working, but sometimes there's also one...November 23th 20251,580
Oven height
When we put a dish or cake in the oven, we naturally tend to put it on the middle shelf, and that's what we usually do. But in some cases, this position and height can be a little tricky, so let's find out why.October 8th 20255,4425
Other pages you may also like
How to zest a fruit?
You will have no doubt noticed that many recipes call for the zest of citrus fruit. The zest is that outer layer of the skin which adds so much flavour to a dish. There are many different ways to peel off the zest and various tools are available. Here is a summary of the “dos and don'ts” of...November 5th 201348 K3.8
Kitchen ovens
You certainly have one in your kitchen, an oven, the essential tool for all kinds of cooking, whether in the kitchen of course, but also in pastry, bakery, pizza, and many others. Here is some information on its structure and operation.May 16th 202035 K4.4
The two frying pans
Where we see that a non-stick frying pan, if it is very practical in general, sometimes it is not enough.February 26th 202212 K4.7
Toss the salad
When you've finished preparing a salad, green or otherwise, it's usually time to add the dressing and toss. It's often said to "toss the salad", which means to season and mix. Is it easy? Not so easy...March 8th 202413 K5
Add a bay leaf
Bay leaf: small in size, but big in flavor. You'll find it in hundreds of recipes, and it's often added to cooking meat, in a sauce or broth, usually accompanied by other herbs or products. It's a staple of Provençal, Mediterranean and Oriental cuisine, but not the only one. Usually, in a...July 31th 20257,0615
Post a comment or question
Follow this page
If you are interested in this page, you can "follow" it, by entering your email address here. You will then receive a notification immediately each time the page is modified or a new comment is added. Please note that you will need to confirm this following.
Note: We'll never share your e-mail address with anyone else.
Alternatively: you can subscribe to the mailing list of cooling-ez.com , you will receive a e-mail for each new recipe published on the site.









